Web and App Security Guide 2021 – Biggest Threats, Vulnerabilities and Prevention Toolkits
The current era is when the IT system has got a lot more complicated than it was in the past, and with every time, this system is getting even more complicated. Each day thousands of different websites and applications are formed, and with businesses getting digitized, different risk factors have evolved along with it.
These websites and applications are holding your precious data, and any cyber threat or security risks may cause you with loss of data worth millions of dollars. Some of the Attacks are:
Cyber-Security Attack:
Online attack or illegal access to users’ information to expose, alter, disable, destroy or even steal data is referred to as cyber-security attack.
Deceptive Phishing Attacks:
How to identify?
- Email from any known senders.
- Hacking information from legitimate & imitating providers.
Solution:
- User should inspect URL carefully.
- Legitimate redirection check-up.
Little help: Look for grammar mistakes, generic salutations, spell errors.
Techniques used by Phisers.
- Legitimate links.
- Blend malicious and benign code.
- Redirects and shortened links.
- Brand logos Obfuscations or Modification.
- Minimal email content.
Spear Phishing Attack:
Social Media sites especially LinkedIn are most infected in this phising techniques.
How to identify?
- Sender will be recognizable.
- Uses personalized information.
Solution:
- Train employee on security awareness.
- Make sure to not share any personal information.
- Take initiative on investment on automated solution for analyzing emails.
Scams Identifications.
- Illegitimate Contact Requests
- Fake Job Offers
- Phishing and Whaling Ploys
- Tech Support Ruses
- Advanced Fee/Inheritance Schemes
Vishing Attack:
How to identify?
Target using telephonic contacts. Vishing campaigns are usually done when phisers instead of sending out an email goes for placing a phone calls.
Hackers can perpetrate a vishing campaign by setting up a (VoIP) server for mimic entities for hacking sensitive data , credentials or funds.
Solutions:
- Do not attend any unknown number call.
- Avoid giving any personal information on phone.
Techniques Used in Vishing by Phisers.
- Mumble Techniques.
- Usage of Technical Jargons.
- Spoofing ID.
Solutions for Preventing attacks:
Digital signature and timestamp service:
Timestamp provides reliability and integrity to a digital signature even after the credentials has been expired or revoked thus enabling long-term validity of digital signatures.
ICA Validation Gateway-VG:
The ICA Validation Gateway-VG allows government, organisations and individuals to utilise their legally valid Emirates ID card for approved/pre-defined online/digital operations.
Fraud CEO using Whaling Attack:
- Targets Executive.
- Used for transferring authorize fraudulent financial.
- Obtain W-2 information on all employees.
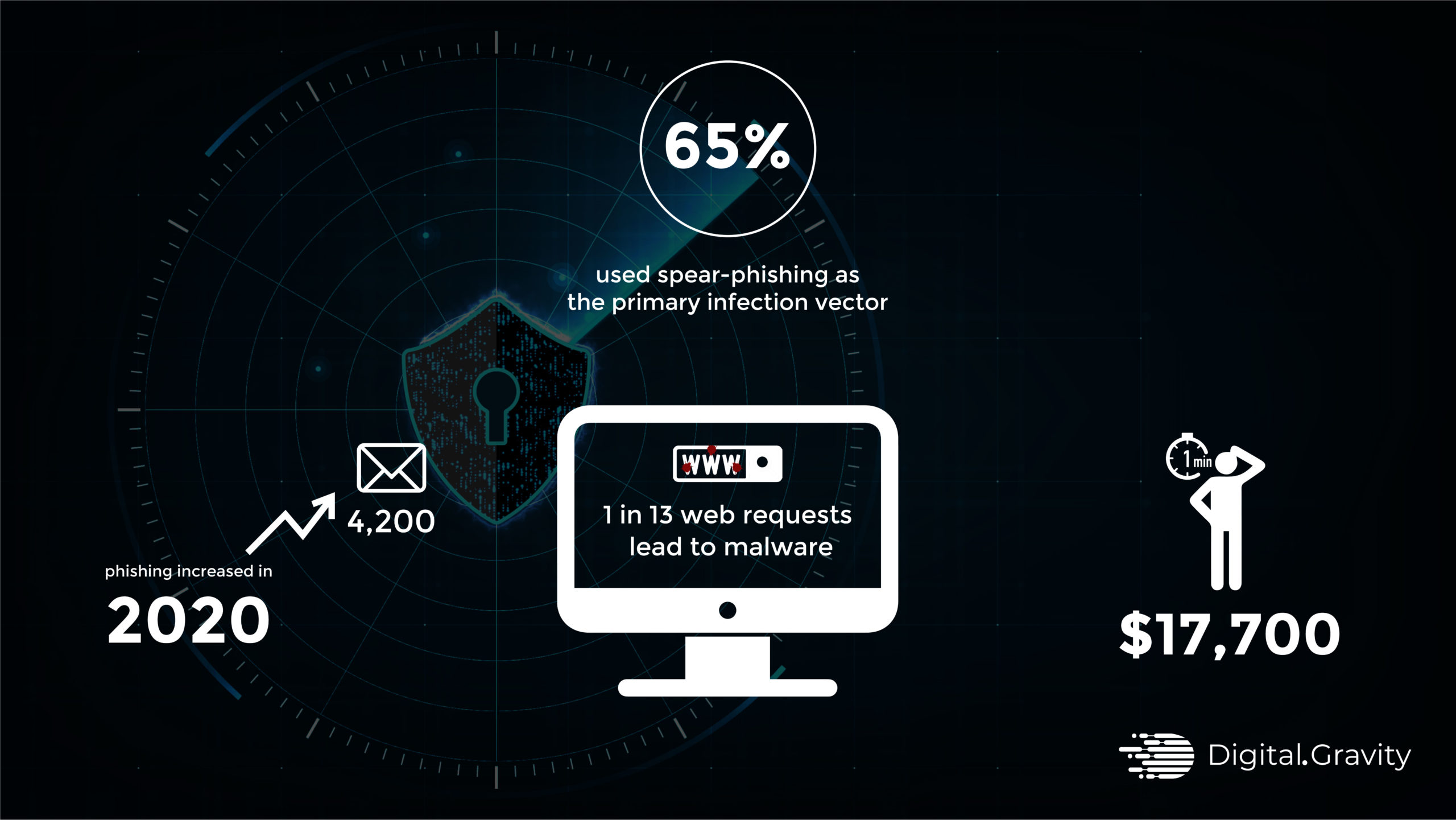
According to varonis some stats for cyber security are:
4,200 emails from attackers are increased with phishing attacks.
65% of phishing attackers used spear-phising as the primary infect vector.
From every 13 of 1 web requests lead to malware attack.
Phishing attacks account for more than 80% of reported security incidents.
Loss of $17,700 money has been lost every minute due to a phishing attack.
What is Malware Attacks?
Malware attack refers to creation of malicious software by cybercriminals. The programmer is involuntary installed on users’ devices to access personal information or damage the device for ransom.
To prevent these security threats, it is essential to understand the possible threats to your Websites and applications and how to prevent them. Below are a few of the common threats that website or app owners have to face.
Best Antivirus Software’s for Malware Attacks:
For malware attacks these are best antivirus software to consider.
Bitdefender – #1 antivirus of 2021
- Rating – 9.8
- Virus Detection Capabilities – Excellent
- System Performance & Operation – Excellent
- Antivirus & Security Features – Excellent
- Product Value for Money – Excellent
- Real-time System & Software Protection
- Guaranteed removal of Malware, Spyware Adware
- 100% Protection against ransom-ware, phishing and fraud
- Rescue mode enabled
- Offers VPN and safer online banking
- Robust Firewall, webcam protection, vulnerability scanner, social network protection
- Strong and secure password manager
- Data shredding and battery mode
- Offer phone support and live chat
- Compatible with Windows, Mac, Linux, Android & iOS mobile apps.
Norton Antivirus – High-accuracy with virus detection, low impact on system performance
- Rating – 9.3
- Virus Detection Capabilities – Excellent
- System Performance & Operation – Satisfactory
- Antivirus & Security Features – Excellent
- Product Value for Money – Satisfactory
- Real-time System Protection
- Guaranteed removal of Malware, Spyware Adware
- 100% Protection against ransom-ware, phishing and fraud
- Offers VPN and safer online banking
- Robust Firewall, webcam protection, vulnerability scanner, social network protection
- Strong and secure password manage
- Data shredding and battery mode
- Offer phone support and live chat
- Compatible with Windows, Mac, Linux, Android and Ios
BullGuard – Fast, efficient & affordable
- Rating – 9.2
- Virus Detection Capabilities – Excellent
- System Performance & Operation – Excellent
- Antivirus & Security Features – Satisfactory
- Product Value for Money – Satisfactory
- Real-time System Protection
- Guaranteed removal of Malware, Spyware Adware
- 100% Protection against phishing and fraud
- Robust Firewall
- Data shredding and battery mode
- Supports live chat
- Compatible with Windows, Mac and Android
McAfee – A lighter yet highly accurate and secure antivirus for all computers
- Rating – 9.2
- Virus Detection Capabilities – Satisfactory
- System Performance & Operation – Satisfactory
- Antivirus & Security Features – Satisfactory
- Product Value for Money – Fair
- Real-time System & Software Protection
- Guaranteed removal of Malware, Spyware Adware
- 100% Protection against ransom-ware, phishing and fraud
- Rescue mode enabled
- Strong and secure password manager
- Data shredding
- Offer phone support and live chat
- Compatible with Windows, Mac, Linux, Android and iOS mobile apps
Panda – Powerful security
- Rating – 9.0
- Virus Detection Capabilities – Fair
- System Performance & Operation – Satisfactory
- Antivirus & Security Features – Satisfactory
- Product Value for Money – Satisfactory
- Real-time System
- Guaranteed removal of Malware, Spyware Adware
- 100% Protection against ransom-ware, phishing and fraud
- Rescue mode enabled
- Robust Firewall, webcam protection
- Strong and secure password manager
- Offer phone support and live chat
- Compatible with Windows, Mac, Linux, Android and iOS mobile apps
Threat and Prevention of SQL Injection
The first thing comes first, and that is SQL Injection.
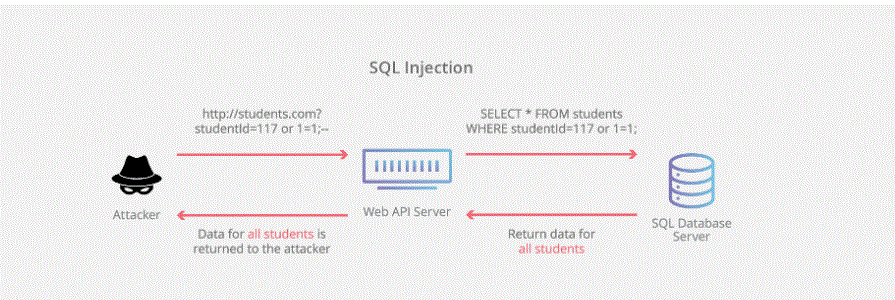
What is SQL injection?
Here is how this process works. After connecting to the database server, SQL map also lets you access all database files and tables from your server.
If you want to know more about SQL injection , here is a complete guide for this.
This is one of the primary and high-risk threats to your system. This is a cyber attack executed by a hacker who tries to gain access to the back-end code of the application or website. After this, he tries to either alter, update, or delete the code to either get access to your data or delete it from your database. This whole process goes without even authorization, so it will be done already till you find out the reasons for data loss.
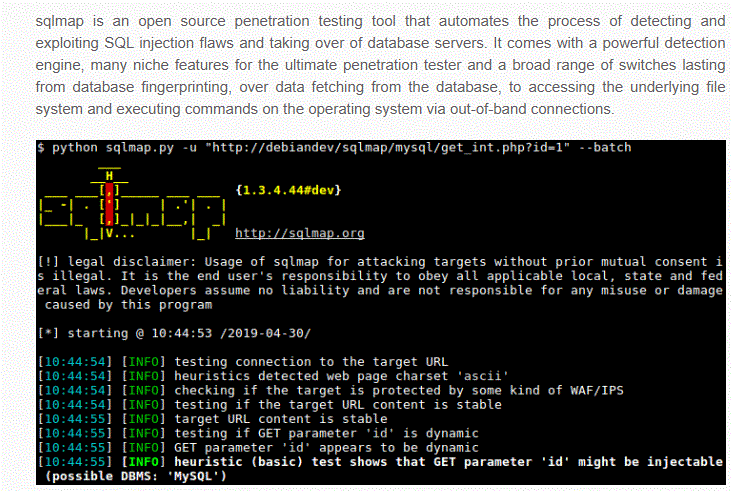
SQLmap Tool:
Now obviously, you might be looking for a tool that would help you to prevent this vulnerability.
You can SQLmap manual here. So, SQLmap is one such tool that is very popular among web developers and owners.
This tool allows you to take complete control over your website’s data and prevent anyone from getting access to your back-end code.
This tool also gets access to the database server, which blocks unauthorized access to your website or app.
This tool can prevent different kinds of SQL injection threats, including time blind injection, Boolean blind injection, stacked queries, and the UNION query.
Broken Authentication Vulnerability and Its Prevention
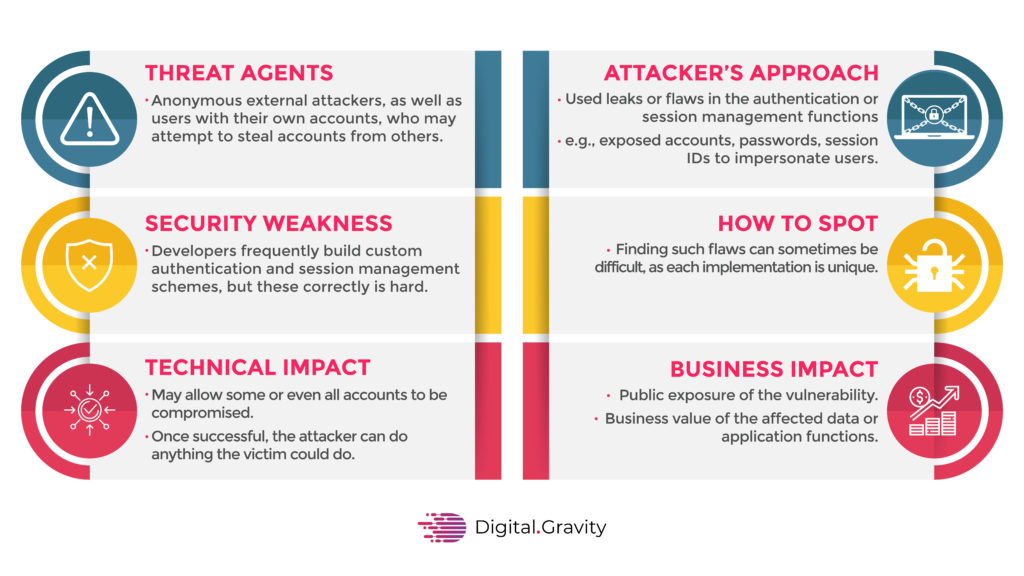
Broken Authentication is one of the common security threats that most users have to face. This is not just a single threat, but basically, it is a whole set of those vulnerabilities that could occur to your app or website.
Broken authentication arise when mobile apps functionality are not implemented properly. Understanding Threat Agents, attack Vectors, security Weakness , Technical Impact Business Impacts through this diagram will help understand how security is being threaten.
Broken authentication is type of threat where an attacker will hack your session, and then from there, he will get your identity which later can be used against you for different purposes.
The first and foremost threat you might have to face is when hackers will obtain your username and password, which they can use to access all of your data.
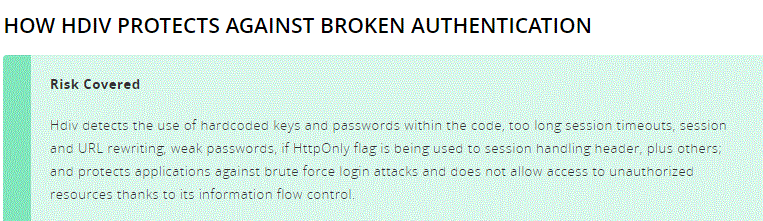
Hdiv protection against Broken Authentication:
If you are looking for a solution to this threat, then specific methods can be followed.
- Activate dual-factor Authentication or security for your database, as it allows just the owner to access the database or code for any update or change.
- Always keep password strength to the maximum because a weak password is readily detectable and vulnerable. Similarly, keep track of any failed login attempts because someone unauthorized may be trying to get into your website database.
In this case, block that IP from ever trying to sign in to your app database. Last but not least is to use Hdiv because this tool covers different weak links in the chain.
Then it helps you restore all those weak links and provide you strong passwords, effective URLs, and block any unauthorized access.
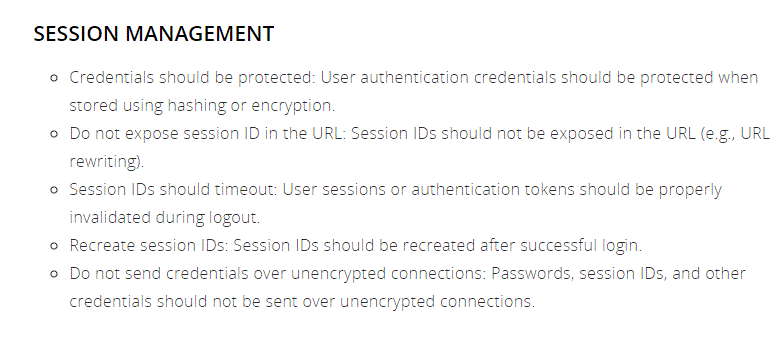
Session should be managed properly
Some points to consider for prevention of broken authentication:
Security Misconfiguration Threat and Prevention
Security Misconfiguration is all about an improper website or app configuration or when you do not pay enough attention to them.
If you are unaware about security misconfigurations, here are some points presented by OWASP:
This would then lead to several other vulnerabilities, including activating folder permissions to everyone, default sign in would be used, debugging is enabled, and other similar vulnerabilities that would let the attacker steal your data or modify it according to him.
Security misconfiguration catalogues for remediation with vulnerability manager Plus
If you were expecting a default security setup for your app, it is not possible, and you have to apply some extra security measures for this purpose.
So, you can start with few simple security measures from your end, which includes disabling Debugging, all unauthorized access to the server should be blocked instantly, routine security scan should be done to find any possible misconfiguration, all default accounts should be disabled, and last but not least Hdiv tools should be used.
This tool is undoubtedly helpful for multiple security threats to your applications and prevents any unofficial login from accessing your application’s data or configurations.
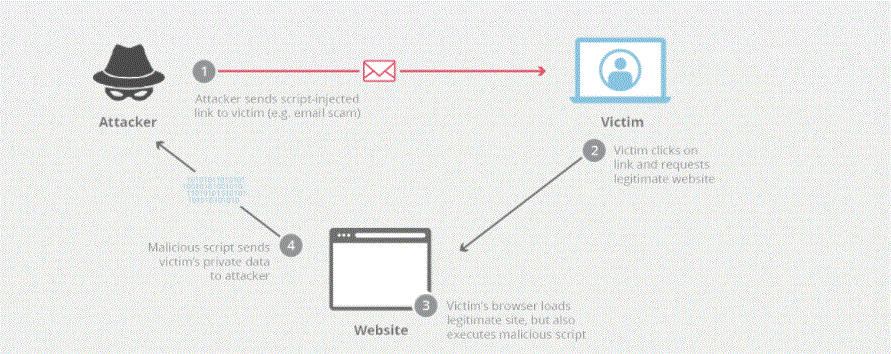
Cross-Site Scripting Vulnerability and Prevention
XSS is another harmful threat for the application users because with this, a hacker attempts to inject a code to the User code, and due to that code, he can change the app output, according to him.
Visually described how attacker injects the malicious scripting in website code by Cloud flare:
The user might not even realize that he is falling under the hacker’s attack, and he will access your session and even redirect you to different malicious websites that will harm your whole system with virus attacks.
If you want to save yourself from any such threat, you would require a tool like Burp Suite Scanner, and this tool then further scans for the whole app database to find Cross-site scripting vulnerabilities.
For future there are some predictions here discussed in Top 21 security predictions for 2021. For security some top progressive web apps development companies mainly focus on the quality product with considering all the malicious attackers with its solution. Well now you do have some vision of how to tackle the attackers, if you are developer who loves to develop a website and mobile apps you should give a read to this blog especially dedicated to Google Products.
According to UAE stats regarding Cyber Attacks & Security:
Proof Point research stated about cyber security especially targeted to UAE region.
In the UAE, 75% organisations offer essential cyber-security training to their employees only twice a year or even less
Survey statistics – Employees make a business more vulnerable to cyber attacks
• 61% – No
• 39% – Yes
Survey statistics – Cyber-security awareness/training sessions offered to employees by organisations in the UAE
• 02% – In Progress/Program in Execution Phase
• 02% – Nil/Not Working
• 23% – 3-4-times per year
• 43% – Twice per year
• 30% – Once a year
Survey Statistics – Biggest cyber-security threats to organisations: Expert prediction till 2024
• Compromised cloud-based accounts (Office 365 and/or Google G-Suite) for instance – 29%
• DDoS Attack – 28%
• Phishing & Fraud – 19%
• Compromised corporate email accounts/Impersonation attacks – 16%
• Ransomware – 15%
• Credential Phishing (stealing user ID/email address and password combinations by masquerading) – 13%
• Internal-Insider Threat/Data Leak-Exposure – 13%
• Nation-Wide Attack/Public cyber-attack – 13%
• Zero/No Threat – 3%
CISCO’s Cyber Security Strategy Audit
• 5% – Nil/Not Executed
• 19% – Less than a single or less than once per year
• 26% – Once in a year
• 40% – Twice per year
• 10% – 3-4 times in a year
Survey Statistics – Cyber-Security Tech: Implementation challenges to organisations in the UAE
• 31% – Lack of board-level/leadership/executive involvement
• 29% – Lack of cyber security threat awareness to businesses
• 23% – Cyber-security: Essential Skills and Training Shortfalls
• 23% – Insufficient budget
• 7% – Zero/No Challenges
The UAE’s National Cyber Security Strategy
– Building a Resilient Infrastructure
– Creating a Safer Cyberspace
– Developing a Vibrant Cyber-security Ecosystem
– Strengthening International Partnership
– Boost defence to safeguard networks, system, functions and data
– Invest in Next Generation Infrastructure
Some strategy implemented in Dubai regarding cyber security
– Leverage Information and Communications Technology Providers as Cybersecurity Enablers
– Improve Incident Reporting and Response
– Modernize Electronic Surveillance and Computer Crime Laws
– Incentivize an Adaptable and Secure Technology Marketplace
– Prioritize Innovation
– Implementing cyber laws
– Promote Full-Lifecycle Cybersecurity
– Build a Cyber Deterrence Initiative
– Counter Malign Cyber Influence and Information Operations
Practical Strategies to Enhance IT Security in UAE
– Support cyber-security staff
– Conduct staff awareness training
– Risk assessment prioritisation
– Regular audit and update IT policies and Procedures
– On-going assessment and improvisation
Cyber-Security budget Increase – Prediction till 2023
• 01% – 51-100% Increase
• 18% – 21-50% Increase
• 50% – 11-20% Increase
• 23% – 1-10% Increase
• 5% – No Increase/Remains the Same
• 3% – Decline/Decrease in Budget
Some prevention hints for any business which should be consider :
eSignature:
Encrypted data in electronic form that’s logically and legally associated with miscellaneous information in digital format, only accessible by the signatory or authority is referred to as electronic signature.
Digital Certificates:
A mathematical procedure or decryption technique to validate integrity and authenticity of a digital document, message or software is referred to as a digital signature.
Digital certification service provider (DCSP):
A government-based, licensed and approved legal entity or an individual that issues digital certificates as well as offer services relevant to digital signature.
How to apply for a DCSP license?
– Company’s memorandum & Articles of Association
– Organisational & Leadership/Board Members structure – Organogram
– Authorized commercial license giving you rights to act as a DCSP
– A legal statement of commercial activities
– Complete date on company’s financial resources and active accounts tracking back to two years or less
– Insurance policy that covers your activities as a DCSP